Your systems must resist all attacks – hackers only need to be lucky once.
Today’s Internet is full of automated attacks that look for vulnerabilities in all public IP addresses. Even modern secure networks may contain vulnerabilities that were unknown at the time of implementation. It is the false sense of perfect security that ultimately causes significant financial losses and usually damage to an organization’s reputation.
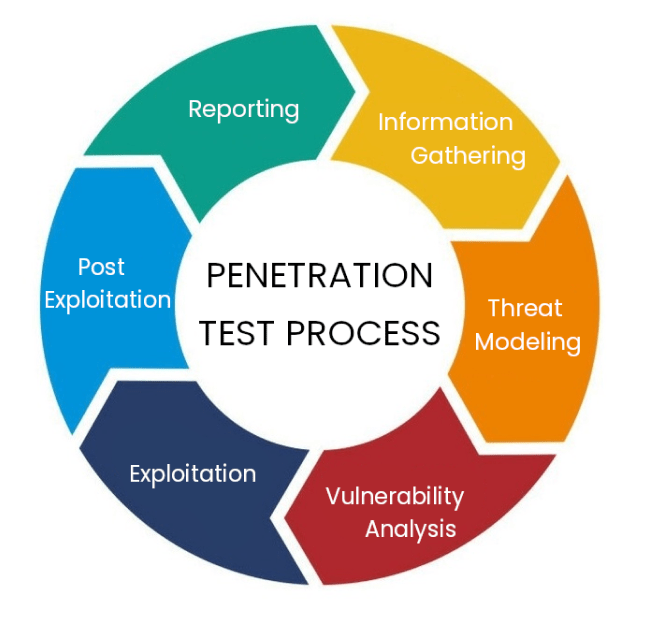
There are many ways to test, but if you don’t want to worry about coming up with your own scenarios, take inspiration from some of the ones below. Our ethical hackers use the OSSTM methodology and their best practices.
Simulation of an attack from the position of a regular user station (domain account without admin access).
TESTING PHASE:
SIMULATION OF AN ATTACK. FROM THE POSITION OF A COMPANY VISITOR:
In this scenario, we verify that access networks intended for guests who do not have their own user account are fully isolated. This includes access from meeting rooms, unprotected Ethernet sockets in corridors and other locations.
Exploring the possibility of infiltration from the external environment without knowledge of the network. These tests target exposed devices and applications to the public Internet.
Tests are generally performed using the black-box method.
TESTING PHASE:
Pentest wireless networks will verify the security of the configuration against unauthorized access, detect rogue Rogue APs, test filtering between LAN segments, and more.
The same methodology is used as for the external test, plus the configuration shortcomings of the cloud provider are examined.
Each penetration test is followed by a phase of documenting the entire test process, describing any vulnerabilities found and rating their severity according to the CVSS classification.
This is the technical part of the report, which is intended for security managers, engineers and application developers, where for each vulnerability a recommendation is also given on how to prevent or solve the problem.
At the end of the report, you will find a management summary that explains in an understandable way to the company’s management the vulnerabilities and security gaps found, their severity and ways to fix any problems.
On request, we can send you a sample of the resulting report.

Contact us using the contact form and our specialist will get back to you within 24 hours.
U Sluncové 666/12a
186 00, Praha 8